FAQ



PLAN IT BUILD IT RUN IT
Most Frequent Questions
We are always available to answer all your queries with regards to storing, managing and protecting data with solutions and services
Losing your data is more common than you might think. It is important to plan and implement Data Protection strategy for every business to avoid data loss and downtime. If you don’t have backups, right now is a high time to plan and implement your very own backup strategy. So what’s the best backup plan and where do you begin? The 3-2-1 backup strategy, of course!
This backup strategy entails, as you might have guessed, three components:
- 3 copies of your data including primary.
- 2 copies on different storage types.
- 1 backup off-site
*Additional solutions like Air-Gapped and Immutable Storage should be implemented for highest level of security and governance.
*Having mechanisms to make sure backups and recovery verification can be done regularly is also very important for integrity.
Data protection is the process of safeguarding important data from corruption, compromise or loss and providing the capability to restore the data to a functional state should something happen to render the data inaccessible or unusable.
Data protection assures that data is not corrupted, is accessible for authorized purposes only, and is in compliance with applicable legal or regulatory requirements. Protected data should be available when needed and usable for its intended purpose.
The scope of data protection, however, goes beyond the notion of data availability and usability to cover areas such as data immutability, preservation, and deletion/destruction.
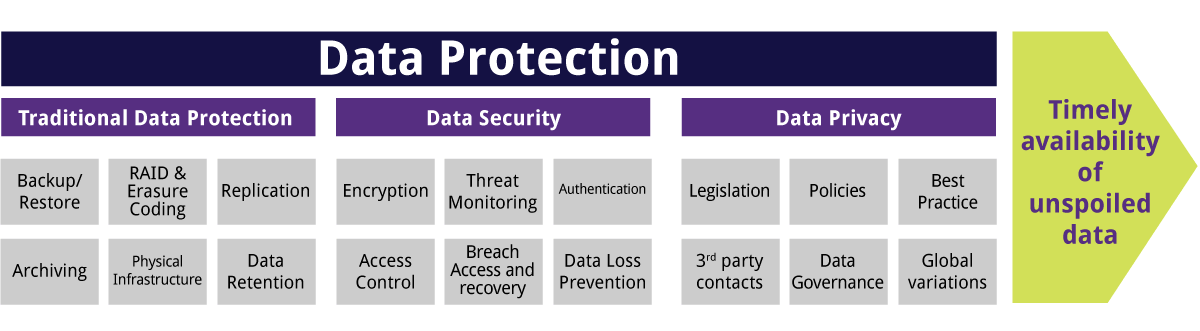
Roughly speaking, data protection spans three broad categories, namely, traditional data protection (such as backup and restore copies), data security, and data privacy as shown in the Figure below. The processes and technologies used to protect and secure data can be considered as data protection mechanisms and business practices to achieve the overall goal of continual availability, and immutability, of critical business data.
With data storage space, users can save data onto a device. And should the computer power down, the data is retained. And instead of manually entering data into a computer, users can instruct the computer to pull data from storage devices. Computers can read input data from various sources as needed, and it can then create and save the output to the same sources or other storage locations. Users can also share data storage with others.
Today, organizations and users require data storage to meet today’s high-level computational needs like big data projects, artificial intelligence (AI), machine learning and the internet of things (IoT). And the other side of requiring huge data storage amounts is protecting against data loss due to disaster, failure or fraud. So, to avoid data loss, organizations can also employ data storage as backup solutions.
In simple terms, modern computers, or terminals, connect to storage devices either directly or through a network. Users instruct computers to access data from and store data to these storage devices. However, at a fundamental level, there are two foundations to data storage: the form in which data takes and the devices data is recorded and stored on.
To store data, regardless of form, users need storage devices. Data storage devices come in two main categories: direct area storage and network-based storage.
Direct area storage, also known as direct-attached storage (DAS), is as the name implies. This storage is often in the immediate area and directly connected to the computing machine accessing it. Often, it’s the only machine connected to it. DAS can provide decent local backup services, too, but sharing is limited. DAS devices include floppy disks, optical discs—compact discs (CDs) and digital video discs (DVDs)—hard disk drives (HDD), flash drives and solid-state drives (SSD).
Network-based storage allows more than one computer to access it through a network, making it better for data sharing and collaboration. Its off-site storage capability also makes it better suited for backups and data protection. Two common network-based storage setups are network-attached storage (NAS) and storage area network (SAN).
Popular types of storage devices:
- SSD and flash storage
- Hybrid storage
- Cloud storage
- Deduplication Appliance
- Tape Library
Data can be recorded and stored in three main forms: file storage, block storage and object storage.
File storage
File storage, also called file-level or file-based storage, is a hierarchical storage methodology used to organize and store data. In other words, data is stored in files, the files are organized in folders and the folders are organized under a hierarchy of directories and sub directories.
Block storage
Block storage, sometimes referred to as block-level storage, is a technology used to store data into blocks. The blocks are then stored as separate pieces, each with a unique identifier. Developers favor block storage for computing situations that require fast, efficient and reliable data transfer.
Object storage
Object storage, often referred to as object-based storage, is a data storage architecture for handling large amounts of unstructured data. This data doesn’t conform to, or can’t be organized easily into, a traditional relational database with rows and columns. Examples include email, videos, photos, web pages, audio files, sensor data, and other types of media and web content (textual or non-textual).
Ransomware is a malware attack that uses a variety of methods to prevent or limit an organization or individual from accessing their IT systems and data, either by locking the system’s screen, or by encrypting files until a ransom is paid, usually in cryptocurrency for reasons of anonymity.
By encrypting these files and demanding a ransom payment for the decryption key, the malware places organizations in a position where paying the ransom is the easiest and most cost-effective way to regain access to their files. It should be noted, however, that paying the ransom does not guarantee that users will get the decryption key required to regain access to the infected system or files.
In some instances, the perpetrators may steal an organization’s information and demand an additional payment in return for not disclosing the information to authorities, competitors or the public, something that would inflict reputational damage to the organization.
The cybercriminals who commit ransomware cybercrimes are now becoming so proficient at what they do that they use artificial intelligence in analyzing the victim’s environment to ensure that recovering files is extremely difficult if not impossible. Additionally, cybercriminals are offering RaaS (ransomware-as-a-service) to organized crime and government agencies to help them launch an attack while they reap the benefits. That may explain why large organizations, which theoretically have large sums of money to pay ransoms, are currently more likely to be targeted than individuals.
However, the landscape is changing, and ransomware is no longer just about a financial ransom with attacks being aimed at public services, utilities and infrastructure undermining public confidence.
Cloud Storage is a conglomeration of highly-scalable data storage, data access, and data management services created to conduct business or consumer-related commerce. Cloud storage provides near-universal access to data with proper access controls implemented for security and reliability. Cloud Storage can be provided as private (in your own data center on your equipment) or public (at someone else’s data center on shared equipment) or a combination of the two.
For the IT organization or IT professional, Cloud Storage can be used to streamline access to data both inside and outside the organization. Cloud Storage implementations (such as public and private cloud) can be combined with localized enterprise storage to enhance flexibility and potentially reduce costs of overall data storage.
For the small business or consumer, Cloud Storage is a model that can be used to greatly simplify storage environments. This could include:
- Deploying storage to the cloud to reduce costs
- Increasing accessibility and ensure availability
- Enhancing storage security
- Using “as a service” components
- Reducing the time to flexibly add storage capacity to any enterprise environment
Linear Tape File System (LTFS) provides an industry standard format for recording data on modern magnetic tape.
LTFS is a file system that allows files stored on magnetic tape to be accessed in a similar fashion to those on disk or removable flash drives. LTFS refers to both the format of data recorded on magnetic tape media and the implementation of specific software that uses this data format to provide a file system interface to data stored on magnetic tape.
Magnetic tape data storage has been used for over 50 years, but typically did not hold file metadata in a form easy to access or modify independent of the file content data. Often external databases were used to maintain file metadata (file names, timestamps, directory hierarchy) to hold this data but these external databases were generally not designed for interoperability and tapes might or might not contain an index of their content.
The standard is based around a self-describing tape format originally developed by IBM.
The LTFS specification became part of the SNIA family of standards in 2012, donated by IBM to SNIA in order to become an open SNIA standard.
Fibre Channel is a high-speed data transfer protocol that provides in-order, lossless delivery of raw block data. It is designed to connect general purpose computers, mainframes and supercomputers to storage devices. The technology primarily supports point-to-point (two devices directly connected to each other) though most common found in switched fabric (devices connected by Fibre Channel switches) environments.
A storage area network (SAN) is a dedicated network used for storage connectivity between host servers and shared storage – typically shared arrays that deliver block-level data storage.
Fibre Channel SANs are typically deployed for low latency applications best suited to block-based storage, such as databases used for high-speed online transactional processing (OLTP), such as those found in banking, online ticketing, and virtual environments. Fibre Channel typically runs on optical fiber cables within and between data centers but can also run on copper cabling.
Fibre Channel is a high-speed data transfer protocol that provides in-order, lossless delivery of raw block data to connect data storage to host servers. Fibre Channel fabrics can be extended over distance for Disaster Recovery and Business Continuance and most SANs are typically designed with redundant fabrics.
NVM Express (NVMe™) is the standard host controller interface for systems using PCI Express (PCIe) based Solid State Drives (SSDs). With the participation of over 120 member companies in NVM Express®. NVMe is architected from the ground up for PCIe SSDs to be efficient, scalable, and manageable, and is also ideal for hyper-converged infrastructure storage.
The first NVMe specification was published in 2011. Since then, there have been three NVMe specifications published with multiple revisions: NVMe, NVMe Management Interface (NVMe-MI™) and NVMe over Fabrics (NVMe-oF™).
The NVM Express base specification defines an interface that provides optimized command submission and completion paths. The interface supports parallel operations with up to 64k I/O Queues and up to 64k outstanding commands per I/O Queue. The interface scales for multi-core CPUs, with few clock cycles needed per I/O operation. The specification also includes end-to-end data protection, enhanced error reporting, and virtualization support.
The NVM Express Management Interface is the command set for in-band and out-of-band management of NVMe storage systems. These management functions include, but are not limited to, discovering, monitoring, and updating firmware on SSDs. NVMe-MI provides an industry-standard way to manage NVMe drives and devices.
The NVMe over Fabrics Drive Specification defines a protocol interface and related extensions that enable the NVMe commands to be transmitted over other interconnects, including RDMA, Fibre Channel, and TCP. NVMe-oF extends the NVMe deployment from local host to remote host(s) for a scale-out NVMe storage system.
These specifications are continuously evolving to new revisions to provide more features and functionalities to support increasing demand for NVMe based storage solutions.
Egestas pretium aenean pharetra magna. Sodales ut eu sem integer vitae justo eget magna. Mattis aliquam faucibus purus in massa tempor nec feugiat. Dolor purus non enim praesent elementum facilisis leo vel fringilla.
Modern data backup software’s are capable to protect every form and type of hardware and software hosted digital information in business data centers.Types of data that can be protected are be at different levels metioned below:
- Filesystem Level – (Ex: NTFS, FAT32, REFS, XFS, ZFS, JFS2, ZFS etc..)
- Operating system Level – (Ex: Windows, Linux, AIX, Solaris, HP-UX etc…)
- Virtual Machine Level – (Ex: Vmware VM, HyperV VM, Nutanix, RHEL VM etc..)
- Cloud Instance Level – (Ex: AWS, Azure, GCP, IBM Cloud etc..)
- Application Level – (Ex: MS Exchange, MS Sharepoint, Domino, SAP HANA etc..)
- Database Level – (Ex: Oracle, DB2, MSSQL, MYSQL, POSTGRESQL, SYBASE etc..)
- Storage Level – (Ex: SAN Storage Snapshot, NAS NDMP, NAS File Proxy etc..)
Professional Services
Do you have any other questions?
Get in touch with our data storage and data protection specialists to get all your queries addressed and challenges resolved by delivering best-in-class industry leading data solutions and certified professional services.

Adipiscing elit duis
We provide our clients with industrial, technical, and creative experience
Sed blandit libero volutpat sed cras ornare arcu dui. At erat pellentesque adipiscing commodo elit at. Condimentum id venenatis a condimentum vitae sapien pellentesque habitant.
Adipiscing elit duis tristique sollicitudin nibh. Hac habitasse platea dictumst vestibulum rhoncus. Faucibus turpis in eu mi. Fermentum odio eu feugiat pretium.

